The UK Government has imposed sanctions on Russian military intelligence units and 18 individuals following the exposure of a sophisticated cyber espionage campaign targeting Microsoft cloud services.
The National Cyber Security Centre (NCSC) revealed that the Russian Advanced Persistent Threat group APT 28 deployed previously unknown malware called AUTHENTIC ANTICS to steal login credentials and maintain persistent access to victim email accounts.
AUTHENTIC ANTICS Targets Microsoft Cloud Environment
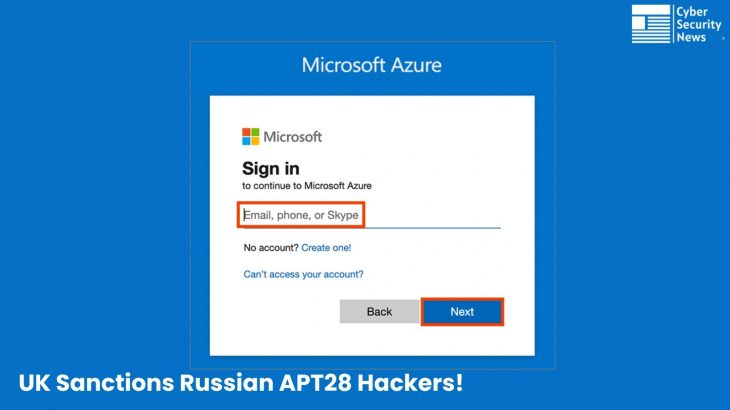
The AUTHENTIC ANTICS malware represents a significant evolution in Russian cyber capabilities, specifically designed to target Microsoft cloud environments through sophisticated credential harvesting techniques.
According to the NCSC’s technical analysis, the malware operates by periodically displaying legitimate-looking login windows that prompt users to enter their credentials.
Once captured, these credentials are intercepted alongside OAuth authentication tokens, which provide the attackers with extended access to Microsoft services without triggering traditional security alerts.
The malware’s stealth capabilities extend beyond simple credential theft. AUTHENTIC ANTICS can exfiltrate sensitive data by automatically sending emails from compromised accounts to actor-controlled addresses while ensuring these messages never appear in the victim’s sent folder.
This technique allows for covert data extraction that can remain undetected for extended periods, enabling long-term intelligence gathering operations.
The UK’s response includes comprehensive sanctions against three GRU units: 26165, 29155, and 74455, along with 18 GRU officers and agents involved in global cyber and information interference operations.
Source: Cybersecurity News