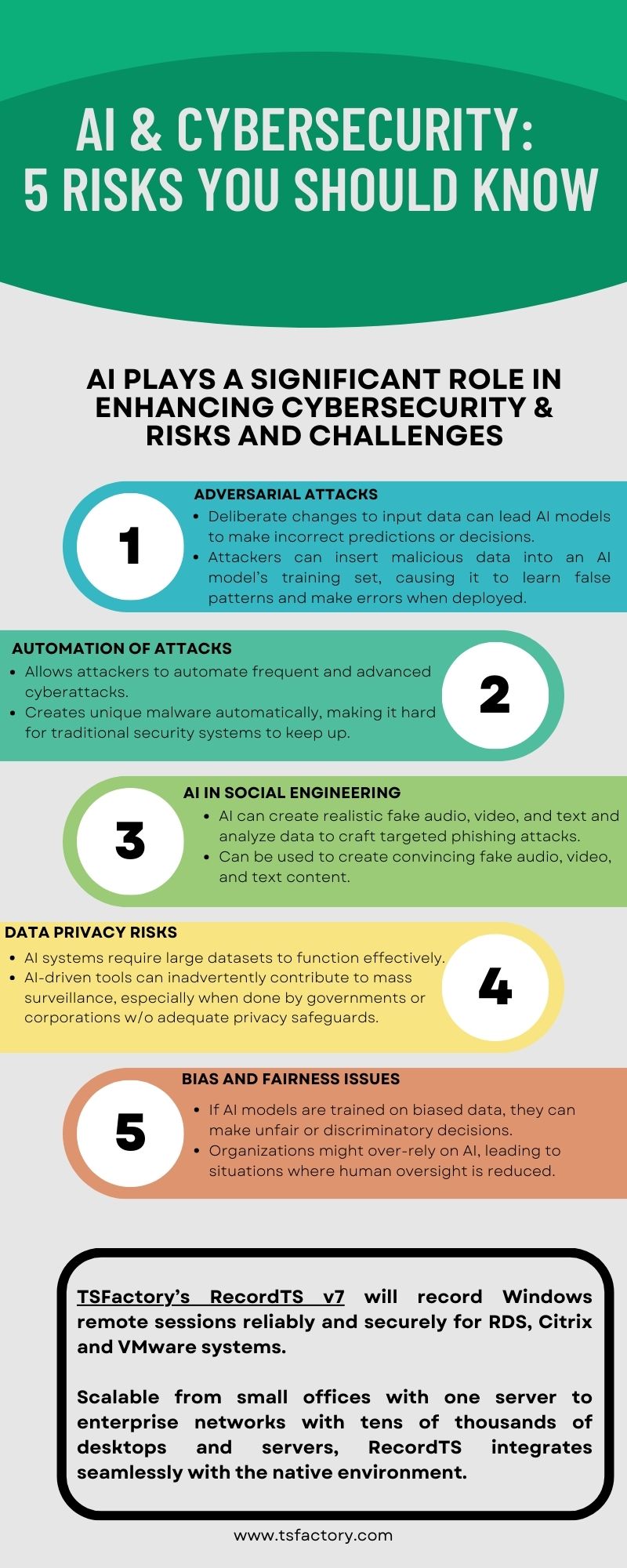
If you recently used your car’s GPS system, relied on auto-correct when writing an email or conducted an online search, chances are you have experienced artificial intelligence (AI). AI also plays a significant role in enhancing cybersecurity, but it also brings a set of risks and challenges. AI in Cybersecurity AI powered cybersecurity can monitor, […]