If you recently used your car’s GPS system, relied on auto-correct when writing an email or conducted an online search, chances are you have experienced artificial intelligence (AI). AI also plays a significant role in enhancing cybersecurity, but it also brings a set of risks and challenges.
AI in Cybersecurity
AI powered cybersecurity can monitor, analyze, detect, and respond to cyber threats in real time. As AI algorithms analyze massive amounts of data to detect patterns that are indicative of a cyber threat, it can also scan the entire network for weaknesses to prevent common kinds of cyber attacks.
How Is AI Cybersecurity Different
AI cybersecurity differs from traditional methods by proactively detecting and responding to threats through real-time behavioral analysis and adaptive learning, rather than relying solely on predefined rules and known threat signatures. This approach enables AI to handle complex, unknown threats more effectively while reducing false positives and automating responses.
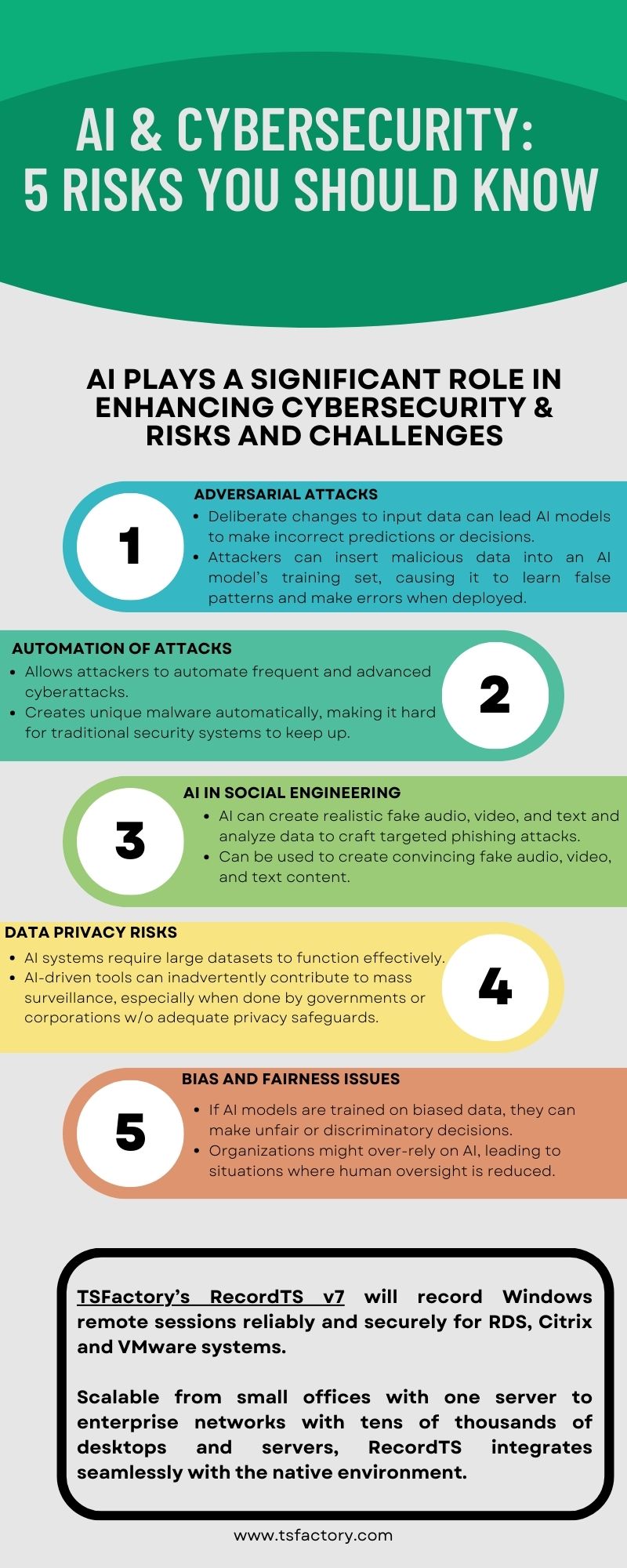
- Adversarial Attacks
- Manipulation of AI Models: AI systems, especially those based on machine learning, can be vulnerable to adversarial attacks. In these attacks, small, intentional perturbations to input data (such as images, network traffic, or even emails) can cause AI models to make incorrect predictions or decisions. Hackers can exploit these weaknesses to bypass security measures.
- Model Poisoning: Attackers may inject malicious data into the training set of an AI model, causing it to learn incorrect patterns and make wrong decisions during deployment. For instance, an AI-based malware detection system could be trained to ignore certain types of malware.
- Automation of Attacks
- Automated Hacking: AI can be used by attackers to automate cyberattacks, making them more frequent and sophisticated. For example, AI can help cybercriminals find vulnerabilities in systems, craft personalized phishing emails, or even conduct large-scale Distributed Denial of Service (DDoS) attacks more efficiently.
- Scalable Attacks: AI-driven tools can be used to scale attacks quickly. For instance, AI can automate the creation of unique malware variants, making it difficult for traditional signature-based security systems to keep up.
- AI in Social Engineering
- Deepfakes and Fake Content: AI technologies, such as deep learning, can be used to create convincing fake audio, video, and text content. This can be used for impersonation in social engineering attacks, leading to fraud, misinformation campaigns, or the manipulation of public opinion.
- Enhanced Phishing: AI can analyze vast amounts of data to craft highly targeted phishing attacks. It can impersonate trusted entities with greater accuracy, making phishing attempts more difficult to detect.
- Data Privacy Risks
- AI Data Collection: AI systems often require large datasets to function effectively. Collecting and storing this data can lead to privacy concerns, as sensitive information might be exposed or misused.
- Invasive Surveillance: AI-driven cybersecurity tools can inadvertently contribute to mass surveillance, especially when deployed by governments or corporations without adequate privacy safeguards.
- Bias and Fairness Issues
- Biased Models: If AI models are trained on biased data, they can make unfair or discriminatory decisions. In cybersecurity, this could result in biased threat detection or unfair targeting of specific groups, potentially leading to civil liberties violations.
- Over-Reliance on AI: Organizations might over-rely on AI, leading to situations where human oversight is reduced. If the AI system has inherent biases or makes incorrect decisions, this could result in significant security breaches or unfair treatment of users.
Conclusion
While AI offers numerous benefits for enhancing cybersecurity, it also introduces significant risks that must be carefully managed. Organizations must ensure that their AI systems are secure, transparent, and used ethically to prevent these risks from undermining their cybersecurity efforts.
Monitoring Remote Sessions
Security monitoring is crucial for preventing ransomware attacks as it enables early detection, identification of vulnerabilities, monitoring for anomalies, data protection, and compliance with regulatory requirements.
TSFactory’s RecordTS v7 will record Windows remote sessions reliably and securely for RDS, Citrix and VMware systems. Scalable from small offices with one server to enterprise networks with tens of thousands of desktops and servers, RecordTS integrates seamlessly with the native environment.