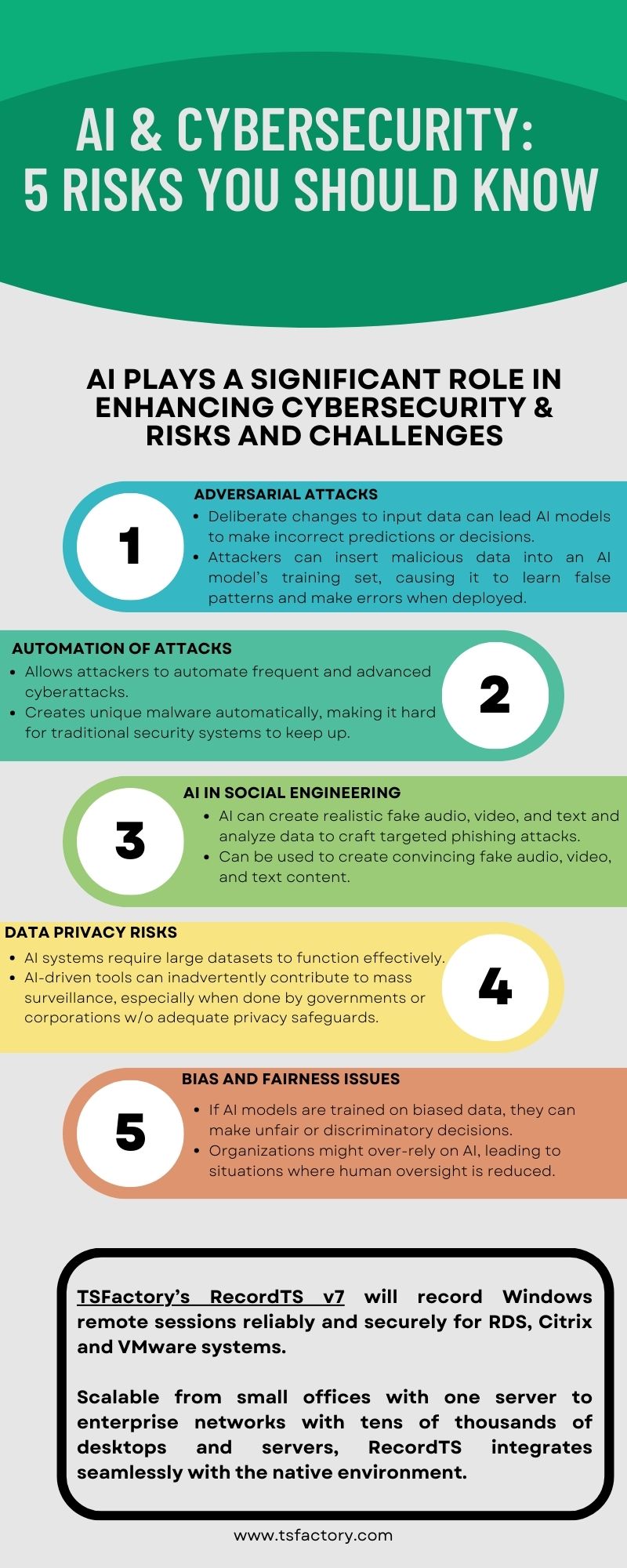
How to Know If Remote Employees Are Working Remote work has become a staple of the modern workplace, offering flexibility and access to global talent. However, for managers, one persistent challenge remains: how to know if remote employees are actually working. Without physical presence and visual cues, it’s easy to feel uncertain about productivity and […]